Mentat
Member-
Posts
119 -
Joined
-
Last visited
-
Days Won
1
Everything posted by Mentat
-
Thank you for this topic. I've installed DSM 7.2 on my very old N54L using the ARC loader and the original onboard NIC. DS3622XS Now It is asking for User Pass User: admin Pass: empty It is not accepted! It is a new installation.
-
DSM 7.1 installation on Intel NUC d54250wyk with MSATA SSD
Mentat replied to Mentat's topic in The Noob Lounge
I know how to activate this add-on on ARPL, but I don't know how to doit on redpill. Any info? -
DSM 7.1 installation on Intel NUC d54250wyk with MSATA SSD
Mentat replied to Mentat's topic in The Noob Lounge
One small problem. If I shutdown the NUC from DSM = Restart -
DSM 7.1 installation on Intel NUC d54250wyk with MSATA SSD
Mentat replied to Mentat's topic in The Noob Lounge
-
Hello! Intel NUC d54250wyk It took a while to make it run. ARPL did not work I use the latest BIOS 0.54, UEFI I use the redpill image Uefi. Write the image on an USB with Balena Etcher. Boot from USB intro Tiny Core and wait to get the IP from DHCP Login via SSH user: tc pass: P@ssw0rd ./rploader.sh update now ./rploader.sh fullupgrade now ./rploader.sh serialgen DS918+ realmac ./rploader.sh identifyusb now ./rploader.sh satamap now IPORTANT! Choose 1 for SATA. If you choose 4, you will get an error on DSM install. ./rploader.sh build ds918p-7.1.1-42962 auto ./rploader.sh clean now rm -rf /mnt/sdb3/auxfiles; rm -rf /home/tc/custom-module; exitcheck.sh reboot A. On the boot select the first option and quicly press e to edit the grub commands. Modify SataPortMap=1 in SataPortMap=4 Press F10 to continue boot. Using Synology Assist find the IP of the NAS and install DSM_DS918+_42962.pat (update 1) On restart apply the same A.metod. if all goes well, shutdown the NAS, extract the USB drive and from a Linux computer (live version) modify grub.cfg forever, with SataPortMap=4. If you want to update to Update 4. Download the Update 4 pat and make the update from the Web interface. On restart, select tinycore and enter via ssh. sudo -i ./rploader.sh postupdate ds918p-7.1.1-42962 ./rploader.sh clean now rm -rf /mnt/sdb3/auxfiles; rm -rf /home/tc/custom-module; exitcheck.sh reboot Press Y on the two questions. Reboot into the first option. Good Luck
-
Intel NUC d54250wyk. I have an M.2 SSD I use the uefi image redpill. "SataPortMap": "1", "DiskIdxMap": "00" ./rploader.sh fullupgrade now ./rploader.sh serialgen DS918+ realmac ./rploader.sh identifyusb now ./rploader.sh satamap now ./rploader.sh build ds918p-7.1.1-42962 auto ./rploader.sh clean now rm -rf /mnt/sdb3/auxfiles; rm -rf /home/tc/custom-module; exitcheck.sh reboot This is the error:
-
RedPill TinyCore Loader Installation Guide for DSM 7.1 BareMetal
Mentat replied to Peter Suh's topic in Tutorials and Guides
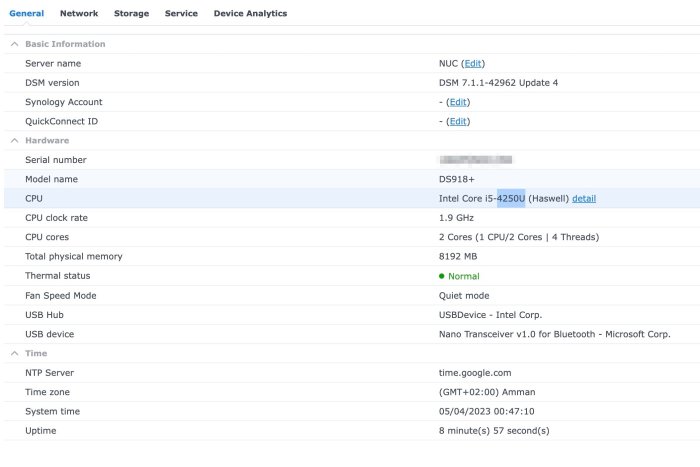
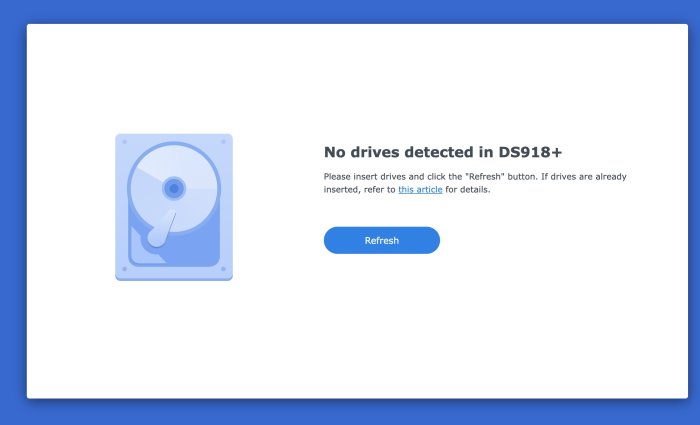
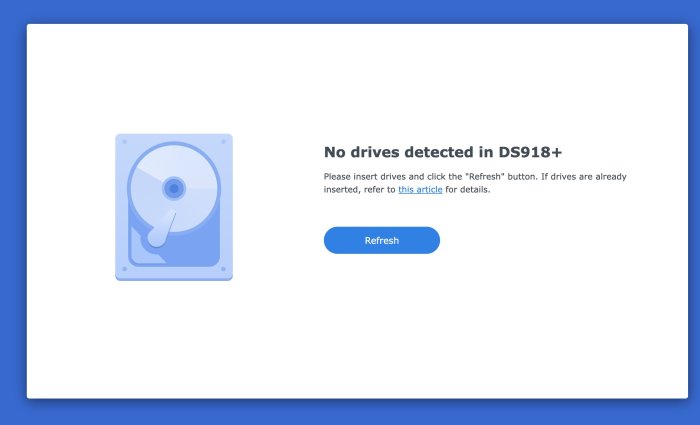
Hello! I have an Intel NUC d54250wyk with an i5-4250U Processor (4th Gen - Haswell). I try to install DSM 7.1 I used the latest UEFI image (is this correct)? It has UEFI "bios". ./rploader.sh update now ./rploader.sh fullupgrade now ./rploader.sh serialgen DS918+ realmac ./rploader.sh identifyusb now ./rploader.sh satamap now ./rploader.sh build ds918p-7.1.1-42962 auto ./rploader.sh clean now rm -rf /mnt/sdb3/auxfiles; rm -rf /home/tc/custom-module; exitcheck.sh reboot "SataPortMap": "1", "DiskIdxMap": "00" I have a very small SSD as storage, but is ok, I don't need storage. The problem is "No Drives detected in DS918+" Please help Thank you -
Hello! I have the same Intel NUC @dhsk1985 Questions: 1. Where can I find redpill-DS918+_7.0.1-42218_b1635406499.img ? 2. I see the content of your grub.cfg What is modified from the default? Thank you
-
DSM 5.x/6.x/7.x CPU name & cores infomation Change tool
Mentat replied to FOXBI's topic in Software Modding
It does not seems to work -
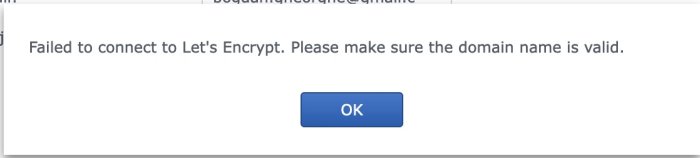
I had DSM 6.2.3 on HP Microserver Gen8 for a sometime and I change Let's encrypt certificate every few months. The story is since 2021, but now it hit me, in 2023! I've tried both versions: cp /etc/ssl/certs/ca-certificates.crt /etc/ssl/certs/ca-certificates.crt.ORIG && curl -k "https://letsencrypt.org/certs/isrgrootx1.pem" >> /etc/ssl/certs/ca-certificates.crt and sudo -i mv /etc/ssl/certs/ca-certificates.crt /etc/ssl/certs/ca-certificates.crt.bak1 curl -Lko /etc/ssl/certs/ca-certificates.crt https://curl.se/ca/cacert.pem curl -k "https://letsencrypt.org/certs/isrgrootx1.pem" >> /etc/ssl/certs/ca-certificates.crt Then reboot, but nothing works. Plus, I've tried to use wget to check on a Let's encrypt site and I still get errors
-
RedPill TinyCore Loader Installation Guide for DSM 7.1 BareMetal
Mentat replied to Peter Suh's topic in Tutorials and Guides
Yes, I have TCRP. from what I see, I must use Jun's Mod for DSM 7.1.1-42962. I there a tutorial for this Mod? Is chaos on the board, please link. -
RedPill TinyCore Loader Installation Guide for DSM 7.1 BareMetal
Mentat replied to Peter Suh's topic in Tutorials and Guides
Well, using the official pat file, now I've managed to install DSM 7.1 and keep all my files intact! Now I have broadwellnk-7.1.0-42661 with update 1 Can I go to a newer version? -
DUMB question... I've just read a tutorial that says to use the offial PAT file to upload on the last step, NOT the one created by TC and downloaded via WiSCP Is this true? :facepalm:
-
I see that this command is executed twice, is this correct? ./rploader.sh build broadwellnk-7.1.0-42661 auto After running all the comands above, I have this in the user_config.json { "extra_cmdline": { "pid": "0x4030", "vid": "0x0424", "sn": "2150xxxxxxLZVN", "mac1": "0011322B4B33", "SataPortMap": "6", "DiskIdxMap": "00" }, "synoinfo": { "internalportcfg": "0xffff", "maxdisks": "16", "support_bde_internal_10g": "no", "support_disk_compatibility": "no", "support_memory_compatibility": "no" }, "ramdisk_copy": {} } Same damn error
-
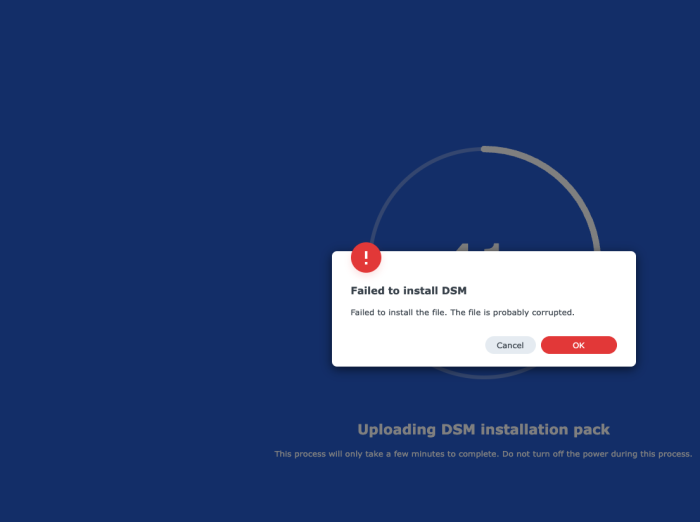
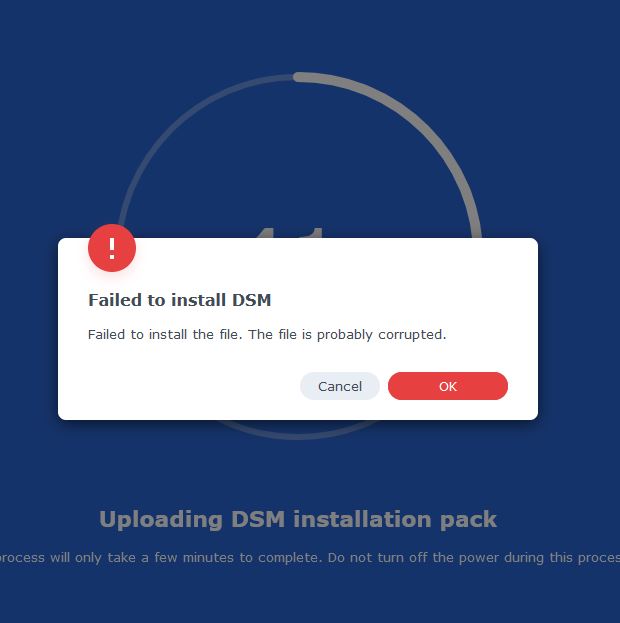
1. There are 4 main HDD. 2. I use the MicroSD card 3. The script detects 6 ports, but I only use 4 HDD. Should I use 4 or 6 in the config? I get corrupted file at ~40%.
-
There are a lot of post here and I do not know where to look. What version do I need to choose? - DS3615XS - What 7.1.xxx DSM? Hardware: Hp Microserver Gen8, Xeon processor, original NIC. I try to install DSM 7.1, but it fails on pat file upload. sudo -i ./rploader.sh update now ./rploader.sh fullupgrade now ./rploader.sh serialgen DS3615xs realmac ./rploader.sh identifyusb now ./rploader.sh satamap now (6 PORTS) ./rploader.sh ext bromolow-7.1.0-42661 ./rploader.sh build bromolow-7.1.0-42661 ./rploader.sh clean now rm -rf /mnt/sdb3/auxfiles; rm -rf /home/tc/custom-module; sudo reboot
-
I've checked the existing certificates and lot are expired, but I do not know if this is the cause ./ssl_check.sh /etc/ssl/certs/ACCVRAIZ1.pem: OK /etc/ssl/certs/ACEDICOM_Root.pem: OK /etc/ssl/certs/AC_Raíz_Certicámara_S.A..pem: OK /etc/ssl/certs/Actalis_Authentication_Root_CA.pem: OK /etc/ssl/certs/AddTrust_External_Root.pem: C = SE, O = AddTrust AB, OU = AddTrust External TTP Network, CN = AddTrust External CA Root error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/AddTrust_Low-Value_Services_Root.pem: C = SE, O = AddTrust AB, OU = AddTrust TTP Network, CN = AddTrust Class 1 CA Root error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/AddTrust_Public_Services_Root.pem: C = SE, O = AddTrust AB, OU = AddTrust TTP Network, CN = AddTrust Public CA Root error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/AddTrust_Qualified_Certificates_Root.pem: C = SE, O = AddTrust AB, OU = AddTrust TTP Network, CN = AddTrust Qualified CA Root error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/AffirmTrust_Commercial.pem: OK /etc/ssl/certs/AffirmTrust_Networking.pem: OK /etc/ssl/certs/AffirmTrust_Premium.pem: OK /etc/ssl/certs/AffirmTrust_Premium_ECC.pem: OK /etc/ssl/certs/ApplicationCA_-_Japanese_Government.pem: C = JP, O = Japanese Government, OU = ApplicationCA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Atos_TrustedRoot_2011.pem: OK /etc/ssl/certs/Autoridad_de_Certificacion_Firmaprofesional_CIF_A62634068.pem: OK /etc/ssl/certs/Baltimore_CyberTrust_Root.pem: OK /etc/ssl/certs/Buypass_Class_2_CA_1.pem: C = NO, O = Buypass AS-983163327, CN = Buypass Class 2 CA 1 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Buypass_Class_2_Root_CA.pem: OK /etc/ssl/certs/Buypass_Class_3_Root_CA.pem: OK /etc/ssl/certs/CA_Disig.pem: C = SK, L = Bratislava, O = Disig a.s., CN = CA Disig error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/CA_Disig_Root_R1.pem: OK /etc/ssl/certs/CA_Disig_Root_R2.pem: OK /etc/ssl/certs/CA_WoSign_ECC_Root.pem: OK /etc/ssl/certs/CFCA_EV_ROOT.pem: OK /etc/ssl/certs/CNNIC_ROOT.pem: OK /etc/ssl/certs/COMODO_Certification_Authority.pem: OK /etc/ssl/certs/COMODO_ECC_Certification_Authority.pem: OK /etc/ssl/certs/COMODO_RSA_Certification_Authority.pem: OK /etc/ssl/certs/Camerfirma_Chambers_of_Commerce_Root.pem: OK /etc/ssl/certs/Camerfirma_Global_Chambersign_Root.pem: OK /etc/ssl/certs/Certification_Authority_of_WoSign_G2.pem: OK /etc/ssl/certs/Certigna.pem: OK /etc/ssl/certs/Certinomis_-_Autorité_Racine.pem: OK /etc/ssl/certs/Certinomis_-_Root_CA.pem: OK /etc/ssl/certs/Certplus_Class_2_Primary_CA.pem: C = FR, O = Certplus, CN = Class 2 Primary CA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Certum_Root_CA.pem: OK /etc/ssl/certs/Certum_Trusted_Network_CA.pem: OK /etc/ssl/certs/Chambers_of_Commerce_Root_-_2008.pem: OK /etc/ssl/certs/China_Internet_Network_Information_Center_EV_Certificates_Root.pem: OK /etc/ssl/certs/ComSign_CA.pem: OK /etc/ssl/certs/Comodo_AAA_Services_root.pem: OK /etc/ssl/certs/Comodo_Secure_Services_root.pem: OK /etc/ssl/certs/Comodo_Trusted_Services_root.pem: OK /etc/ssl/certs/Cybertrust_Global_Root.pem: O = "Cybertrust, Inc", CN = Cybertrust Global Root error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/D-TRUST_Root_Class_3_CA_2_2009.pem: OK /etc/ssl/certs/D-TRUST_Root_Class_3_CA_2_EV_2009.pem: OK /etc/ssl/certs/DST_ACES_CA_X6.pem: C = US, O = Digital Signature Trust, OU = DST ACES, CN = DST ACES CA X6 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/DST_Root_CA_X3.pem: O = Digital Signature Trust Co., CN = DST Root CA X3 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Deutsche_Telekom_Root_CA_2.pem: C = DE, O = Deutsche Telekom AG, OU = T-TeleSec Trust Center, CN = Deutsche Telekom Root CA 2 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/DigiCert_Assured_ID_Root_CA.pem: OK /etc/ssl/certs/DigiCert_Assured_ID_Root_G2.pem: OK /etc/ssl/certs/DigiCert_Assured_ID_Root_G3.pem: OK /etc/ssl/certs/DigiCert_Global_Root_CA.pem: OK /etc/ssl/certs/DigiCert_Global_Root_G2.pem: OK /etc/ssl/certs/DigiCert_Global_Root_G3.pem: OK /etc/ssl/certs/DigiCert_High_Assurance_EV_Root_CA.pem: OK /etc/ssl/certs/DigiCert_Trusted_Root_G4.pem: OK /etc/ssl/certs/E-Tugra_Certification_Authority.pem: OK /etc/ssl/certs/EBG_Elektronik_Sertifika_Hizmet_Sağlayıcısı.pem: CN = EBG Elektronik Sertifika Hizmet Sa\C4\9Flay\C4\B1c\C4\B1s\C4\B1, O = EBG Bili\C5\9Fim Teknolojileri ve Hizmetleri A.\C5\9E., C = TR error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/EC-ACC.pem: OK /etc/ssl/certs/EE_Certification_Centre_Root_CA.pem: OK /etc/ssl/certs/Entrust.net_Premium_2048_Secure_Server_CA.pem: OK /etc/ssl/certs/Entrust_Root_Certification_Authority.pem: OK /etc/ssl/certs/Entrust_Root_Certification_Authority_-_EC1.pem: OK /etc/ssl/certs/Entrust_Root_Certification_Authority_-_G2.pem: OK /etc/ssl/certs/Equifax_Secure_CA.pem: C = US, O = Equifax, OU = Equifax Secure Certificate Authority error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Equifax_Secure_Global_eBusiness_CA.pem: C = US, O = Equifax Secure Inc., CN = Equifax Secure Global eBusiness CA-1 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Equifax_Secure_eBusiness_CA_1.pem: C = US, O = Equifax Secure Inc., CN = Equifax Secure eBusiness CA-1 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/GeoTrust_Global_CA.pem: C = US, O = GeoTrust Inc., CN = GeoTrust Global CA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/GeoTrust_Global_CA_2.pem: C = US, O = GeoTrust Inc., CN = GeoTrust Global CA 2 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/GeoTrust_Primary_Certification_Authority.pem: OK /etc/ssl/certs/GeoTrust_Primary_Certification_Authority_-_G2.pem: OK /etc/ssl/certs/GeoTrust_Primary_Certification_Authority_-_G3.pem: OK /etc/ssl/certs/GeoTrust_Universal_CA.pem: OK /etc/ssl/certs/GeoTrust_Universal_CA_2.pem: OK /etc/ssl/certs/GlobalSign_ECC_Root_CA_-_R4.pem: OK /etc/ssl/certs/GlobalSign_ECC_Root_CA_-_R5.pem: OK /etc/ssl/certs/GlobalSign_Root_CA.pem: OK /etc/ssl/certs/GlobalSign_Root_CA_-_R2.pem: OU = GlobalSign Root CA - R2, O = GlobalSign, CN = GlobalSign error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/GlobalSign_Root_CA_-_R3.pem: OK /etc/ssl/certs/Global_Chambersign_Root_-_2008.pem: OK /etc/ssl/certs/Go_Daddy_Class_2_CA.pem: OK /etc/ssl/certs/Go_Daddy_Root_Certificate_Authority_-_G2.pem: OK /etc/ssl/certs/Hellenic_Academic_and_Research_Institutions_RootCA_2011.pem: OK /etc/ssl/certs/Hongkong_Post_Root_CA_1.pem: OK /etc/ssl/certs/IGC_A.pem: C = FR, ST = France, L = Paris, O = PM/SGDN, OU = DCSSI, CN = IGC/A, emailAddress = igca@sgdn.pm.gouv.fr error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/IdenTrust_Commercial_Root_CA_1.pem: OK /etc/ssl/certs/IdenTrust_Public_Sector_Root_CA_1.pem: OK /etc/ssl/certs/Izenpe.com.pem: OK /etc/ssl/certs/Juur-SK.pem: emailAddress = pki@sk.ee, C = EE, O = AS Sertifitseerimiskeskus, CN = Juur-SK error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Microsec_e-Szigno_Root_CA.pem: C = HU, L = Budapest, O = Microsec Ltd., OU = e-Szigno CA, CN = Microsec e-Szigno Root CA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Microsec_e-Szigno_Root_CA_2009.pem: OK /etc/ssl/certs/NetLock_Arany_=Class_Gold=_Főtanúsítvány.pem: OK /etc/ssl/certs/NetLock_Business_=Class_B=_Root.pem: C = HU, L = Budapest, O = NetLock Halozatbiztonsagi Kft., OU = Tanusitvanykiadok, CN = NetLock Uzleti (Class B) Tanusitvanykiado error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/NetLock_Express_=Class_C=_Root.pem: C = HU, L = Budapest, O = NetLock Halozatbiztonsagi Kft., OU = Tanusitvanykiadok, CN = NetLock Expressz (Class C) Tanusitvanykiado error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/NetLock_Notary_=Class_A=_Root.pem: C = HU, ST = Hungary, L = Budapest, O = NetLock Halozatbiztonsagi Kft., OU = Tanusitvanykiadok, CN = NetLock Kozjegyzoi (Class A) Tanusitvanykiado error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/NetLock_Qualified_=Class_QA=_Root.pem: OK /etc/ssl/certs/Network_Solutions_Certificate_Authority.pem: OK /etc/ssl/certs/OISTE_WISeKey_Global_Root_GA_CA.pem: OK /etc/ssl/certs/OISTE_WISeKey_Global_Root_GB_CA.pem: OK /etc/ssl/certs/PSCProcert.pem: emailAddress = contacto@procert.net.ve, L = Chacao, ST = Miranda, OU = Proveedor de Certificados PROCERT, O = Sistema Nacional de Certificacion Electronica, C = VE, CN = PSCProcert error 20 at 0 depth lookup:unable to get local issuer certificate /etc/ssl/certs/QuoVadis_Root_CA.pem: C = BM, O = QuoVadis Limited, OU = Root Certification Authority, CN = QuoVadis Root Certification Authority error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/QuoVadis_Root_CA_1_G3.pem: OK /etc/ssl/certs/QuoVadis_Root_CA_2.pem: OK /etc/ssl/certs/QuoVadis_Root_CA_2_G3.pem: OK /etc/ssl/certs/QuoVadis_Root_CA_3.pem: OK /etc/ssl/certs/QuoVadis_Root_CA_3_G3.pem: OK /etc/ssl/certs/RSA_Security_2048_v3.pem: OK /etc/ssl/certs/Root_CA_Generalitat_Valenciana.pem: C = ES, O = Generalitat Valenciana, OU = PKIGVA, CN = Root CA Generalitat Valenciana error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/S-TRUST_Authentication_and_Encryption_Root_CA_2005_PN.pem: OK /etc/ssl/certs/S-TRUST_Universal_Root_CA.pem: OK /etc/ssl/certs/SecureSign_RootCA11.pem: OK /etc/ssl/certs/SecureTrust_CA.pem: OK /etc/ssl/certs/Secure_Global_CA.pem: OK /etc/ssl/certs/Security_Communication_EV_RootCA1.pem: OK /etc/ssl/certs/Security_Communication_RootCA2.pem: OK /etc/ssl/certs/Security_Communication_Root_CA.pem: OK /etc/ssl/certs/Sonera_Class_1_Root_CA.pem: C = FI, O = Sonera, CN = Sonera Class1 CA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Sonera_Class_2_Root_CA.pem: C = FI, O = Sonera, CN = Sonera Class2 CA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Staat_der_Nederlanden_EV_Root_CA.pem: OK /etc/ssl/certs/Staat_der_Nederlanden_Root_CA.pem: C = NL, O = Staat der Nederlanden, CN = Staat der Nederlanden Root CA error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Staat_der_Nederlanden_Root_CA_-_G2.pem: C = NL, O = Staat der Nederlanden, CN = Staat der Nederlanden Root CA - G2 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/Staat_der_Nederlanden_Root_CA_-_G3.pem: OK /etc/ssl/certs/Starfield_Class_2_CA.pem: OK /etc/ssl/certs/Starfield_Root_Certificate_Authority_-_G2.pem: OK /etc/ssl/certs/Starfield_Services_Root_Certificate_Authority_-_G2.pem: OK /etc/ssl/certs/StartCom_Certification_Authority.pem: OK /etc/ssl/certs/StartCom_Certification_Authority_2.pem: C = IL, O = StartCom Ltd., OU = Secure Digital Certificate Signing, CN = StartCom Certification Authority error 18 at 0 depth lookup:self signed certificate OK /etc/ssl/certs/StartCom_Certification_Authority_G2.pem: OK /etc/ssl/certs/SwissSign_Gold_CA_-_G2.pem: OK /etc/ssl/certs/SwissSign_Platinum_CA_-_G2.pem: OK /etc/ssl/certs/SwissSign_Silver_CA_-_G2.pem: OK /etc/ssl/certs/Swisscom_Root_CA_1.pem: OK /etc/ssl/certs/Swisscom_Root_CA_2.pem: OK /etc/ssl/certs/Swisscom_Root_EV_CA_2.pem: OK /etc/ssl/certs/T-TeleSec_GlobalRoot_Class_2.pem: OK /etc/ssl/certs/T-TeleSec_GlobalRoot_Class_3.pem: OK /etc/ssl/certs/TC_TrustCenter_Class_3_CA_II.pem: OK /etc/ssl/certs/TURKTRUST_Certificate_Services_Provider_Root_2007.pem: CN = T\C3\9CRKTRUST Elektronik Sertifika Hizmet Sa\C4\9Flay\C4\B1c\C4\B1s\C4\B1, C = TR, L = Ankara, O = T\C3\9CRKTRUST Bilgi \C4\B0leti\C5\9Fim ve Bili\C5\9Fim G\C3\BCvenli\C4\9Fi Hizmetleri A.\C5\9E. (c) Aral\C4\B1k 2007 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/TWCA_Global_Root_CA.pem: OK /etc/ssl/certs/TWCA_Root_Certification_Authority.pem: OK /etc/ssl/certs/Taiwan_GRCA.pem: OK /etc/ssl/certs/TeliaSonera_Root_CA_v1.pem: OK /etc/ssl/certs/Trustis_FPS_Root_CA.pem: OK /etc/ssl/certs/TÜBİTAK_UEKAE_Kök_Sertifika_Hizmet_Sağlayıcısı_-_Sürüm_3.pem: C = TR, L = Gebze - Kocaeli, O = T\C3\BCrkiye Bilimsel ve Teknolojik Ara\C5\9Ft\C4\B1rma Kurumu - T\C3\9CB\C4\B0TAK, OU = Ulusal Elektronik ve Kriptoloji Ara\C5\9Ft\C4\B1rma Enstit\C3\BCs\C3\BC - UEKAE, OU = Kamu Sertifikasyon Merkezi, CN = T\C3\9CB\C4\B0TAK UEKAE K\C3\B6k Sertifika Hizmet Sa\C4\9Flay\C4\B1c\C4\B1s\C4\B1 - S\C3\BCr\C3\BCm 3 error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/TÜRKTRUST_Elektronik_Sertifika_Hizmet_Sağlayıcısı_H5.pem: OK /etc/ssl/certs/TÜRKTRUST_Elektronik_Sertifika_Hizmet_Sağlayıcısı_H6.pem: OK /etc/ssl/certs/USERTrust_ECC_Certification_Authority.pem: OK /etc/ssl/certs/USERTrust_RSA_Certification_Authority.pem: OK /etc/ssl/certs/UTN_USERFirst_Email_Root_CA.pem: C = US, ST = UT, L = Salt Lake City, O = The USERTRUST Network, OU = http://www.usertrust.com, CN = UTN-USERFirst-Client Authentication and Email error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/UTN_USERFirst_Hardware_Root_CA.pem: C = US, ST = UT, L = Salt Lake City, O = The USERTRUST Network, OU = http://www.usertrust.com, CN = UTN-USERFirst-Hardware error 10 at 0 depth lookup:certificate has expired OK /etc/ssl/certs/VeriSign_Class_3_Public_Primary_Certification_Authority_-_G4.pem: OK /etc/ssl/certs/VeriSign_Class_3_Public_Primary_Certification_Authority_-_G5.pem: OK /etc/ssl/certs/VeriSign_Universal_Root_Certification_Authority.pem: OK /etc/ssl/certs/Verisign_Class_1_Public_Primary_Certification_Authority.pem: OK /etc/ssl/certs/Verisign_Class_1_Public_Primary_Certification_Authority_-_G2.pem: OK /etc/ssl/certs/Verisign_Class_1_Public_Primary_Certification_Authority_-_G3.pem: OK /etc/ssl/certs/Verisign_Class_2_Public_Primary_Certification_Authority_-_G2.pem: OK /etc/ssl/certs/Verisign_Class_2_Public_Primary_Certification_Authority_-_G3.pem: OK /etc/ssl/certs/Verisign_Class_3_Public_Primary_Certification_Authority.pem: OK /etc/ssl/certs/Verisign_Class_3_Public_Primary_Certification_Authority_-_G2.pem: OK /etc/ssl/certs/Verisign_Class_3_Public_Primary_Certification_Authority_-_G3.pem: OK /etc/ssl/certs/Verisign_Class_3_Public_Primary_Certification_Authority_2.pem: C = US, O = "VeriSign, Inc.", OU = Class 3 Public Primary Certification Authority error 18 at 0 depth lookup:self signed certificate OK /etc/ssl/certs/Visa_eCommerce_Root.pem: OK /etc/ssl/certs/WellsSecure_Public_Root_Certificate_Authority.pem: OK /etc/ssl/certs/WoSign.pem: OK /etc/ssl/certs/WoSign_China.pem: OK /etc/ssl/certs/XRamp_Global_CA_Root.pem: OK /etc/ssl/certs/certSIGN_ROOT_CA.pem: OK /etc/ssl/certs/ePKI_Root_Certification_Authority.pem: OK /etc/ssl/certs/thawte_Primary_Root_CA.pem: OK /etc/ssl/certs/thawte_Primary_Root_CA_-_G2.pem: OK /etc/ssl/certs/thawte_Primary_Root_CA_-_G3.pem: OK
-
My Xpenology was working smootly (DSM 6.2.3-25426 Update 3) with Jun's loader 1.03b on my HP Microserver Gen8 Out of the sudden, Pi-Hole in the docker started to have problems and also my entire LAN, as it was the DNS. I've managed to fix the network by using Google DNS on the router, but now I have a problem: I cannot acces any https sites from the interface (see Packages) or from SSH. I've copy the newest certificates from https://curl.se/ca/cacert.pem to /etc/ssl/certs/ca-certificates.crt and rebooted, but no luck! I can access my NAS from outside via https, but I cannot access any site via https from my NAS and I have no idea why I have this problem out of the blue. wget https://pkgupdate.synology.com/packagecenter/v2/getList --2022-06-04 22:12:45-- https://pkgupdate.synology.com/packagecenter/v2/getList Resolving pkgupdate.synology.com... 54.192.235.51, 54.192.235.128, 54.192.235.17, ... Connecting to pkgupdate.synology.com|54.192.235.51|:443... connected. Unable to establish SSL connection. curl https://curl.se/ca/cacert.pem curl: (35) OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to curl.se:443
-
I've managed to install 7.0.1, but I cannot upgrade to 7.1
-
RedPill TinyCore Loader Installation Guide for DSM 7.1 BareMetal
Mentat replied to Peter Suh's topic in Tutorials and Guides
Again, I've managed to install 7.0.1-42218 Doing the same steps for 7.1.0-42661 will result in an error (corrupted file). -
RedPill TinyCore Loader Installation Guide for DSM 7.1 BareMetal
Mentat replied to Peter Suh's topic in Tutorials and Guides
My processor is Intel i3 3240 so i think bromolow is the arhitecture ? sudo -i ./rploader.sh update now ./rploader.sh fullupgrade now ./rploader.sh serialgen DS3615xs ./rploader.sh identifyusb now ./rploader.sh satamap now I've choosed 4 SATA ./rploader.sh build bromolow-7.1.0-42661 ./rploader.sh clean now Same error on using the pat file, 41% probably corrupt file, now using USB stick, not microSD. -
RedPill TinyCore Loader Installation Guide for DSM 7.1 BareMetal
Mentat replied to Peter Suh's topic in Tutorials and Guides
Please help, I do no know whre to look for the errors... Hardware: HP Microserver Gen8, 4 SATA HDD, was working with DSM 6.2 Default network NIC (Broadcom) The loader is on the MicroSD card from the MB. I've created the redpill.pad I've downloaded the created pat file with WinSCP Now I boot from redpill (default USB option), I upload the above pat file. I get error that the file is probably corrupted at 41%. And I'm stuck.